Within this post I’ll be doing a write up of the Wide challenge from the HackTheBox Cyber Apocalypse 2022 CTF competition (14/05/2022). This write up will be written according to my thought process whilst I was trying to complete the challenge.
Reconaissance
First look
After I downloaded the file attached to the challenge on the CTF platform, I unpacked the zip file and took a look at the contents. To start off with, there was a binary file called wide and a file called db.ex. I decided to take a look at the wide binary to begin.
Executing the file in the terminal yielded the following output:
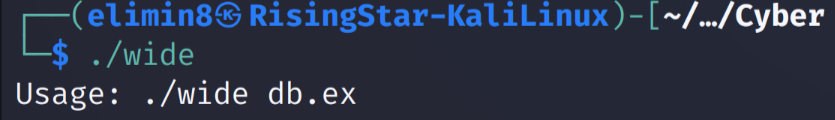
After adding db.ex as a parameter, I ran the command again.
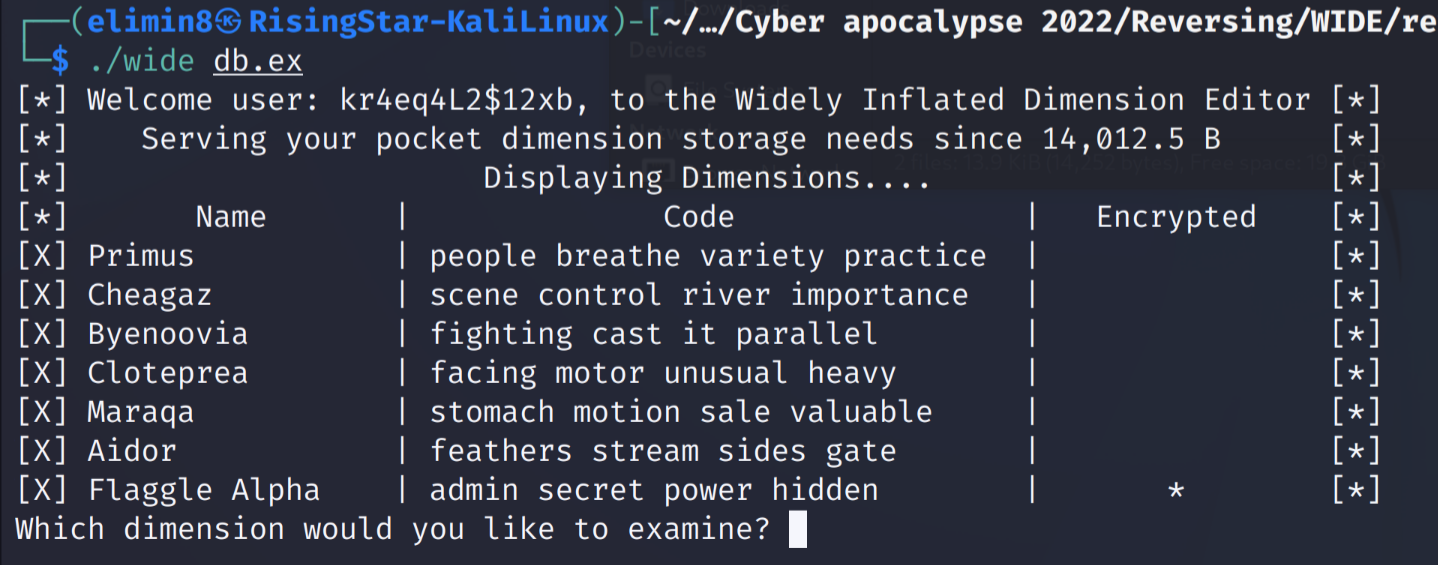
There were several different dimensions I could choose to access in the program, so I tried accessing them one by one and checking them to see if they had anything interesting.
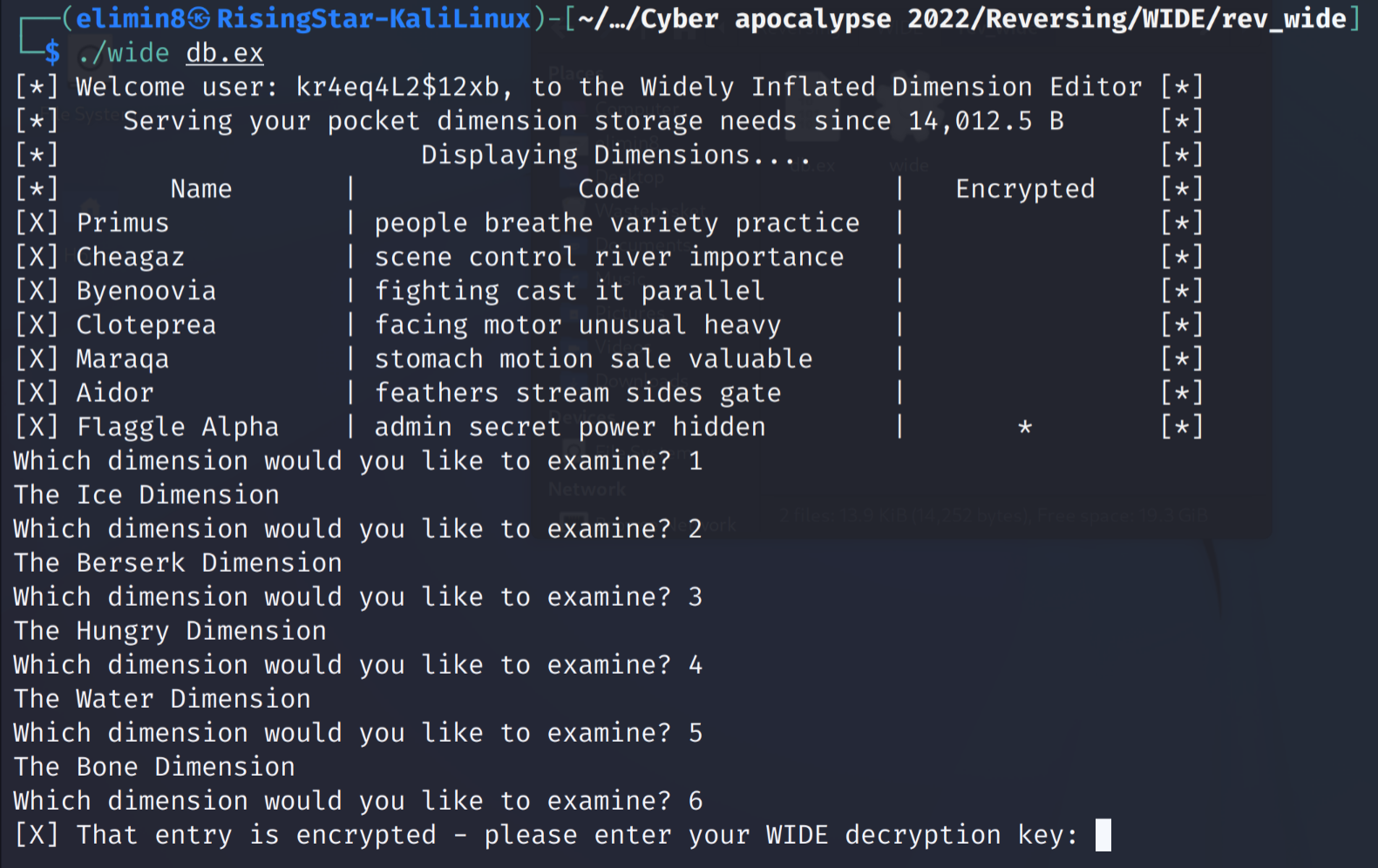
Ah, it seemed that one of them was encrypted and required a password for access. I decided to take a closer look at the wide binary in radare2.
Analysis
After seeking to the main function and printing the disassembled function, I decided to take a look through the instructions. Near the end of the function, the following function call attracted my attention:
|
|
So next I seeked to the ‘sym.menu’ function and printed the contents of that too, with these lines being of particular interest to me:
|
|
It appeared that the section was getting some input from the user using fgets and then comparing it to another string, ‘sup3rs3cr3tw1d3’, which is of type wchar. I wasn’t actually aware of this type of string, so I decided to research it in comparison to other types. Eventually, I came across this wikipedia page which explained that they are effectively characters which have sizes greater than 8 bits and are therefore different to the typical ascii standard. To confirm this, I decided to run strings on the binary and see if the ‘sup3rs3cr3tw1d3’ string would show.
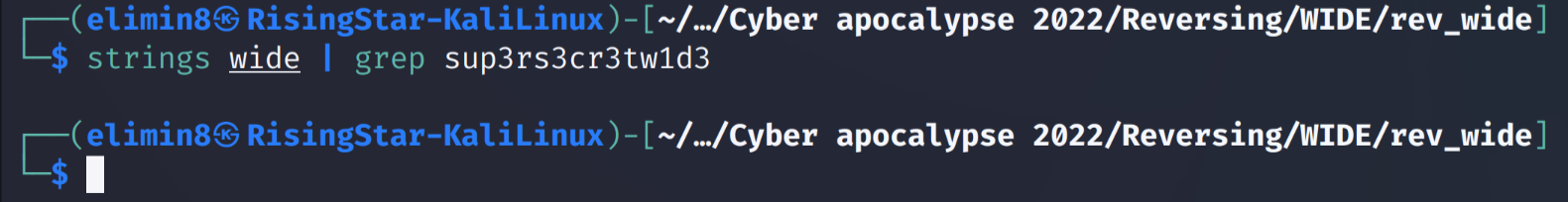
Clearly, strings only looked for ascii strings when it scanning the content of files. Interesting.
Exploitation
Next, I decided to attempt to input the ‘sup3rs3cr3tw1d3’ string as the password when prompted in the program.
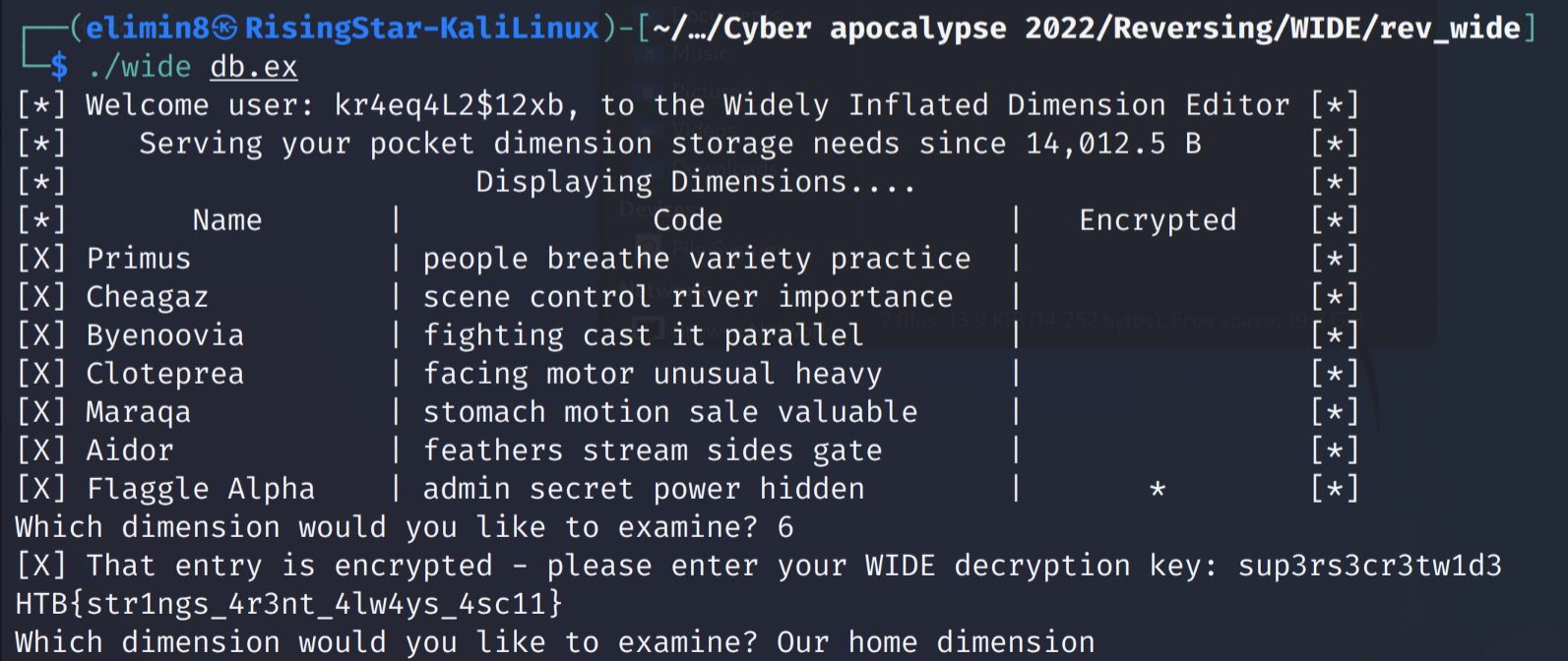
There we go, that was a rather short challenge, but an interesting one nonetheless.
Mitigations
Security by obscurity
The usage of the wchar type in c is not an effective method for storing encryption keys for sensitive content, as despite taking longer for discovery of the key in some circumstances, it’s useless for truly securing the key. Ideally, the key should not be present in the file and the program would simply attempt to decrypt the text with the given password and check for the ‘HTB{’ header in the text to tell if the decryption was successful.
Donate
